I've been off eBay for a while and started using it again recently. It seems like each year that site gets crappier and crappier.
For example, I've had several auctions where the price starts at $0.99. I set my max bid to say $40, which is a fair price for what I'm bidding on. The auction will have 3-4 days left on it. So I'm the highest bidder at $5 or whatever. Then suddenly the auction is cancelled with no reason given!
I know some people used to list an item on Craigslist or something but they'd typically have a Buy It Now price and at least tell you that they were trying to sell it outside of eBay.
The only other option I can think of is the seller decided not to sell the item or worried they weren't going to get their price. But due to bid sniping, you won't know until the final minutes what your final price is going to be near.
Now you bid with the possibility that whatever you bid on can be pulled at any time. If anything, this is making me look for sellers who run "Sell it on eBay" stores or are "professional" eBay auctioneers. Those with low ratings, etc are losing my business because I can't take their auction seriously!
Monday, June 14, 2010
Wednesday, June 2, 2010
Windows Home Server
I've been using Windows Home Server for about six months now and feel comfortable giving it a review now.
Overview
Earlier this year I realized my tech at home was getting out of control. I had a personal desktop, work desktop, laptop, digital camera, digital camcorder, my wife's laptop, XBox 360, camera phones, etc.
I frequently found myself looking across multiple devices to find documents, photos, baby videos, etc. I also found that I had a lot of physical media (Music CDs, DVD movies) that I was storing in cabinets when I could save them to a centralized location and store the physical media in the attic or storage closet.
Originally, my plan was to build a full blown server and setup a domain, shared folders, etc. But, why implement an Enterprise solution for a relatively trivial task.
The solution I decided upon was Windows Home Server.
Getting to WHS
I'd looked at some other free products but didn't find anything I was really enamored with. There were plenty of applications that would allow me to share my content with the XBox and handle MP3s/MPGs. But, these tools didn't handle documents very well. I also wanted some directory security to avoid someone accidentally moving or deleting source code for clients I support while trying to copy some photos. I also wanted to be able to make some content public for friends when they visited and hooked up to the WiFi for example, free software I downloaded and use, but not my taxes and bank statements.
I could have gone with a mixed solution, Active Directory for file management, and another program for media syndication. However, I wanted a product that really integrated seamlessly across all boundaries.
Ultimately, I found WHS would be my best option.
Using WHS
Installing WHS is like any other Windows install you've ever done so there were no surprises there. Well, unless your host machine didn't support modern power management functionality. I ended up having to change out the motherboard on my host machine (a rack mount server) to a compliant board.
Once installed, you really never need to go back into the WHS machine. Instead, you install a "connector" application on the machines you want to use WHS with. I don't recall needing to do anything special for the XBox it just sees the server and can access whatever publicly accessible content is available; pictures, movies, music.
Once installed, the connector shows up as an icon in your system tray. When the server is running and your PC is "healthy" the icon is green. Otherwise it will change colors depending on the situation.
Setting up users and file permissions are very easy. You simple create them using the WHS GUI and assign users rights (none, read, full). It basically handles the active directory type functions for you.
You also get a "Shared Folders" desktop icon to access the Shares you have access to.
There is no magic here, just a simple and easy to use interface for sharing data on your network.
Misc Notes
WHS also automates backups of your machines which is handy if you're looking for a centralized backup solution.
Another cool feature is WHS handles the allocation of the disks for you. Once you mount a drive your disk WHS will automatically handle it. Instead of having physical disks, you have a big virtual disk that expands and is managed by WHS automatically.
Next Steps
For me, my next step is to figure out how to store DVR data on my server. My DVR fills us quickly and I end up having to delete programs I wanted to keep!
Overview
Earlier this year I realized my tech at home was getting out of control. I had a personal desktop, work desktop, laptop, digital camera, digital camcorder, my wife's laptop, XBox 360, camera phones, etc.
I frequently found myself looking across multiple devices to find documents, photos, baby videos, etc. I also found that I had a lot of physical media (Music CDs, DVD movies) that I was storing in cabinets when I could save them to a centralized location and store the physical media in the attic or storage closet.
Originally, my plan was to build a full blown server and setup a domain, shared folders, etc. But, why implement an Enterprise solution for a relatively trivial task.
The solution I decided upon was Windows Home Server.
Getting to WHS
I'd looked at some other free products but didn't find anything I was really enamored with. There were plenty of applications that would allow me to share my content with the XBox and handle MP3s/MPGs. But, these tools didn't handle documents very well. I also wanted some directory security to avoid someone accidentally moving or deleting source code for clients I support while trying to copy some photos. I also wanted to be able to make some content public for friends when they visited and hooked up to the WiFi for example, free software I downloaded and use, but not my taxes and bank statements.
I could have gone with a mixed solution, Active Directory for file management, and another program for media syndication. However, I wanted a product that really integrated seamlessly across all boundaries.
Ultimately, I found WHS would be my best option.
Using WHS
Installing WHS is like any other Windows install you've ever done so there were no surprises there. Well, unless your host machine didn't support modern power management functionality. I ended up having to change out the motherboard on my host machine (a rack mount server) to a compliant board.
Once installed, you really never need to go back into the WHS machine. Instead, you install a "connector" application on the machines you want to use WHS with. I don't recall needing to do anything special for the XBox it just sees the server and can access whatever publicly accessible content is available; pictures, movies, music.
Once installed, the connector shows up as an icon in your system tray. When the server is running and your PC is "healthy" the icon is green. Otherwise it will change colors depending on the situation.
Setting up users and file permissions are very easy. You simple create them using the WHS GUI and assign users rights (none, read, full). It basically handles the active directory type functions for you.
You also get a "Shared Folders" desktop icon to access the Shares you have access to.
There is no magic here, just a simple and easy to use interface for sharing data on your network.
Misc Notes
WHS also automates backups of your machines which is handy if you're looking for a centralized backup solution.
Another cool feature is WHS handles the allocation of the disks for you. Once you mount a drive your disk WHS will automatically handle it. Instead of having physical disks, you have a big virtual disk that expands and is managed by WHS automatically.
Next Steps
For me, my next step is to figure out how to store DVR data on my server. My DVR fills us quickly and I end up having to delete programs I wanted to keep!
Wednesday, May 19, 2010
Application Security Overview
Overview
I rarely find an organization who has someone whose sole job is to ensure the security of data and applications across an Enterprise. Therefore, a lot of that job falls on the shoulders of developers. I think security is a rather broad topic with a lot of considerations but for the purposes of this blog... I'll stick to some basic scenarios.
Really, there are two major scenarios to consider in regards to security; the data and transport of the data.
Transport Security
The most basic and reasonable method of securing your data from point A to point B is to use a mechanism like SSL. Normally in HTTP, data is sent in a clear text format. Using SSL, both client and server agree on a key to use and the data is sent in an encrypted form across the wire where it is decrypted on the other end. As you would imagine, this process does increase the size of your payload being sent and returned but prevents someone who intercepts the packets from viewing the contents without first breaking the encryption.
The performance bottleneck is one of the reasons you see merchant sites unsecured until you switch over to process a payment, at which time SSL is employed.
Data Security
When securing your data, you have options but need to choose carefully. For example, if you encrypt data in the database that field is no longer searchable by the database engine. Additionally, as with SSL there is the performance hit of decrypting. Lastly, you have to consider reporting and other functionality that may have no/limited abilities to decrypt data.
Presently, Rijndael is a popular encryption algorithm and works pretty well. You will have to specify two key values (key and IV) in order to encrypt and decrypt data. However, both the source and destination machine must have the same keys otherwise this won't work. A practical application of this might be to encrypt data going between two machines across the internet via a web service. (Tho again, SSL can also be used... so Rijndael would be an added layer of protection if that was the case.) This might also be useful when passing a token to a non-secured web service to authenticate.
On a machine, I like to use DPAPI. This came integrated in Framework 2.0 (IE, there are objects for it you can use) and encrypts data with a key specific to the machine. This is great for securing connection string and other components of your app or web config file. I'm not going to go into detail but basically you can use the ProtectedData class (part of System.Security.Cryptography) with LocalMachine protection scope.
Alternately, you could do a DLLImport and use the encryption DLLs directly but this approach is frowned upon since it creates unmanaged code.
Recap
Use SSL to protect data in transit from server to client; HTTP is clear/plain text by default.
Use Rijndael to encrypt/decrypt sensitive data; remember you can't search encrypted database fields.
Use DPAPI to encrypt data with a machine specific algorithm.
I rarely find an organization who has someone whose sole job is to ensure the security of data and applications across an Enterprise. Therefore, a lot of that job falls on the shoulders of developers. I think security is a rather broad topic with a lot of considerations but for the purposes of this blog... I'll stick to some basic scenarios.
Really, there are two major scenarios to consider in regards to security; the data and transport of the data.
Transport Security
The most basic and reasonable method of securing your data from point A to point B is to use a mechanism like SSL. Normally in HTTP, data is sent in a clear text format. Using SSL, both client and server agree on a key to use and the data is sent in an encrypted form across the wire where it is decrypted on the other end. As you would imagine, this process does increase the size of your payload being sent and returned but prevents someone who intercepts the packets from viewing the contents without first breaking the encryption.
The performance bottleneck is one of the reasons you see merchant sites unsecured until you switch over to process a payment, at which time SSL is employed.
Data Security
When securing your data, you have options but need to choose carefully. For example, if you encrypt data in the database that field is no longer searchable by the database engine. Additionally, as with SSL there is the performance hit of decrypting. Lastly, you have to consider reporting and other functionality that may have no/limited abilities to decrypt data.
Presently, Rijndael is a popular encryption algorithm and works pretty well. You will have to specify two key values (key and IV) in order to encrypt and decrypt data. However, both the source and destination machine must have the same keys otherwise this won't work. A practical application of this might be to encrypt data going between two machines across the internet via a web service. (Tho again, SSL can also be used... so Rijndael would be an added layer of protection if that was the case.) This might also be useful when passing a token to a non-secured web service to authenticate.
On a machine, I like to use DPAPI. This came integrated in Framework 2.0 (IE, there are objects for it you can use) and encrypts data with a key specific to the machine. This is great for securing connection string and other components of your app or web config file. I'm not going to go into detail but basically you can use the ProtectedData class (part of System.Security.Cryptography) with LocalMachine protection scope.
Alternately, you could do a DLLImport and use the encryption DLLs directly but this approach is frowned upon since it creates unmanaged code.
Recap
Use SSL to protect data in transit from server to client; HTTP is clear/plain text by default.
Use Rijndael to encrypt/decrypt sensitive data; remember you can't search encrypted database fields.
Use DPAPI to encrypt data with a machine specific algorithm.
Delegates
I thought I posted this a while back but it doesn't appear on my list of blogs so I'm reposting it.
A delegate is what used to be called a function pointer in C++. What it basically allows you to do is define the method signature of a function that is going to be called at run time without knowing what the function is at compile time.
Where this is useful is in cases where you have object(s) that need to register to be notified when something happens so it can take the proper action. This may sound a lot like an event; that's because an event is basically a variant of a delegate.
Two special types of delegates are the anonymous and multi-cast.
The anonymous is where you delcare a delegate but you define the function to be called inside the delegate declaration. Example: button1.Click += delegate(System.Object o, System.EventArgs e)
{ System.Windows.Forms.MessageBox.Show("Click!"); };
So we're targeting a method that accepts object, EventArgs but we're actually defining the implemenation inside the declaration. So this delegate, when fired, would display Click! in a message box.
In the multi-cast delegate, you can target multiple method(s). But I don't recall ever using this feature so I don't have an example of it.
The most common place I use delegates is when I'm trying to filter a List of items. I normally use an anonymous delegate.
So assume I have a class, Employee with a FirstName field... and I've stored all my Employee records inside a List called MyList.
Example: List MyListOfBobs = MyList.FindAll(delegate(Employee e){return e.FirstName == "Bob";});
So here I would get back all the employees in MyList where the FirstName was equal to Bob.
I could also do something like this... MyList.FindAll(FindAllBobsMethod);
private static bool FindAllBobsMethod(Employee e)
{
if (e.FirstName == "Bob")
return true;
else
return false;
}
A delegate is what used to be called a function pointer in C++. What it basically allows you to do is define the method signature of a function that is going to be called at run time without knowing what the function is at compile time.
Where this is useful is in cases where you have object(s) that need to register to be notified when something happens so it can take the proper action. This may sound a lot like an event; that's because an event is basically a variant of a delegate.
Two special types of delegates are the anonymous and multi-cast.
The anonymous is where you delcare a delegate but you define the function to be called inside the delegate declaration. Example: button1.Click += delegate(System.Object o, System.EventArgs e)
{ System.Windows.Forms.MessageBox.Show("Click!"); };
So we're targeting a method that accepts object, EventArgs but we're actually defining the implemenation inside the declaration. So this delegate, when fired, would display Click! in a message box.
In the multi-cast delegate, you can target multiple method(s). But I don't recall ever using this feature so I don't have an example of it.
The most common place I use delegates is when I'm trying to filter a List
So assume I have a class, Employee with a FirstName field... and I've stored all my Employee records inside a List called MyList.
Example: List
So here I would get back all the employees in MyList where the FirstName was equal to Bob.
I could also do something like this... MyList.FindAll(FindAllBobsMethod);
private static bool FindAllBobsMethod(Employee e)
{
if (e.FirstName == "Bob")
return true;
else
return false;
}
Tuesday, May 18, 2010
Partial Classes
The concept of the partial class came into play in Framework 2.0. However, I've noticed that people have either forgotten or didn't notice this handy keyword.
Framework 1.0
If you used the 1.0 Frameworks you noticed when you created UI elements that all the back-end code for those controls ended up going into the form's code behind. Typically, this resided in a region called something like "Designer Generated Code".
To me at least, this cluttered your code behind with code that was required but not it wasn't YOUR code.
Framwork 2.0
The solution to this and many other problems came in the 2.0 release of the Framework with this new keyword; partial.
A partial class essentially is a keyword that tells the compiler "hey, my class is defined across several definitions; usually across multiple files". It almost reminds of me header files in C++, but that's neither here nor there.
You can use partial on a class, struct, or interface.
So what?
Well, the two reasons MSDN's documentation suggests using the partial keyword are the same two reasons I like it.
1. It keeps system generated code in its own section away from your code.
2. (This is the big one...) Allows teams of developers to break a class into several logical files to reduce/prevent waiting on your code to be checked in to edit a section.
Like I said, reason 2 is my favorite. Countless times I've needed to add an item to an enum, add an overload of a function to a class... and its checked out. I would even say in about 90% of the cases, the other developer was changing things unrelated to what I wanted to change!
My rule of thumb is to break the code into logical chunks when using a partial class. For example, if I had an ATM object then I might break each class into the functions the ATM can perform. Obviously, the class name will be the same but I like to use a classname_function type name for all the partial files.
Example:
ATM.cs (maybe where I keep the constructor, declarations, and properties)
ATM_Withdraw.cs
ATM_Deposit.cs
ATM_GetStamps.cs
ATM_PrintStatement.cs
Usage
Using the partial keyword is easy! Simply put "partial" after the scope (public, private, protected,etc) and before the type (class, interface, enum).
Example:
public partial class Form1 : Form
Note: This would be the main declaration of the class. A subsequent declaration wouldn't need the inherits. So your other partials would like like this: public partial class Form1
Other Considerations
Keep in mind that the entire class definition has to be in the SAME namespace.
All parts must have the same scope (accessibility). IE, its public or private, etc not mix and match.
Framework 1.0
If you used the 1.0 Frameworks you noticed when you created UI elements that all the back-end code for those controls ended up going into the form's code behind. Typically, this resided in a region called something like "Designer Generated Code".
To me at least, this cluttered your code behind with code that was required but not it wasn't YOUR code.
Framwork 2.0
The solution to this and many other problems came in the 2.0 release of the Framework with this new keyword; partial.
A partial class essentially is a keyword that tells the compiler "hey, my class is defined across several definitions; usually across multiple files". It almost reminds of me header files in C++, but that's neither here nor there.
You can use partial on a class, struct, or interface.
So what?
Well, the two reasons MSDN's documentation suggests using the partial keyword are the same two reasons I like it.
1. It keeps system generated code in its own section away from your code.
2. (This is the big one...) Allows teams of developers to break a class into several logical files to reduce/prevent waiting on your code to be checked in to edit a section.
Like I said, reason 2 is my favorite. Countless times I've needed to add an item to an enum, add an overload of a function to a class... and its checked out. I would even say in about 90% of the cases, the other developer was changing things unrelated to what I wanted to change!
My rule of thumb is to break the code into logical chunks when using a partial class. For example, if I had an ATM object then I might break each class into the functions the ATM can perform. Obviously, the class name will be the same but I like to use a classname_function type name for all the partial files.
Example:
ATM.cs (maybe where I keep the constructor, declarations, and properties)
ATM_Withdraw.cs
ATM_Deposit.cs
ATM_GetStamps.cs
ATM_PrintStatement.cs
Usage
Using the partial keyword is easy! Simply put "partial" after the scope (public, private, protected,etc) and before the type (class, interface, enum).
Example:
public partial class Form1 : Form
Note: This would be the main declaration of the class. A subsequent declaration wouldn't need the inherits. So your other partials would like like this: public partial class Form1
Other Considerations
Keep in mind that the entire class definition has to be in the SAME namespace.
All parts must have the same scope (accessibility). IE, its public or private, etc not mix and match.
Monday, May 17, 2010
Droid 2.1 for HTC Droid Eris
The Verizon update for the HTC Droid Eris has dropped in the last few days. Users will be prompted to install a system update. This will bring your phone to Droid 2.1 and give it many of the features that the Motorola Droid users have been enjoying the last few months.
There are 4 features that I am excited about:
-New support for voice-to-text entry. Whenever a text-entry box appears, simply tap the microphone icon on the virtual keyboard and speak.
-Google Maps with Navigation provides free, traffic-enhanced,turn-by-turn navigation.
-Longer battery life due to power savings.
-Faster power-up time
NOTE: You will need 25mb of free internal memory to install this update. The easiest way to do this is go is to go tnto the System Settings -> Manage Applications and go to the "Browser" application. There will be an option on the page labelled "Clear Cache". If you use your browser much then this folder will probably be over 25MB and now you have the space you need to install.
On my install, I lost all my contacts. Luckily, I do my contacts through Gmail. All I had to do was force a sync of my contacts with Gmail and I was back in business. One quirk was that a few contacts (Husbands / Wives who share a Facebook account) were merged into a single contact.
There are 4 features that I am excited about:
-New support for voice-to-text entry. Whenever a text-entry box appears, simply tap the microphone icon on the virtual keyboard and speak.
-Google Maps with Navigation provides free, traffic-enhanced,turn-by-turn navigation.
-Longer battery life due to power savings.
-Faster power-up time
NOTE: You will need 25mb of free internal memory to install this update. The easiest way to do this is go is to go tnto the System Settings -> Manage Applications and go to the "Browser" application. There will be an option on the page labelled "Clear Cache". If you use your browser much then this folder will probably be over 25MB and now you have the space you need to install.
On my install, I lost all my contacts. Luckily, I do my contacts through Gmail. All I had to do was force a sync of my contacts with Gmail and I was back in business. One quirk was that a few contacts (Husbands / Wives who share a Facebook account) were merged into a single contact.
Friday, May 14, 2010
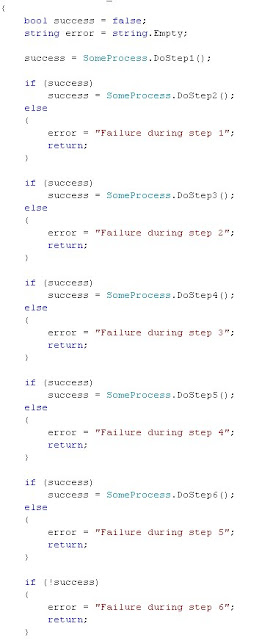
How To Write Clean Multi-Step Code
Scenario
You have a process with some number of steps and each step must complete successfully before the next step can continue. A scenario I've seen before in peer reviews and production code is a nested set of IF statements to determine if the next step should be processed, etc.
I've provided a simple (yet verbose example) of what this code might look like below.
Notice that we're checking each call to see if the previous call worked. As you also may see we are duplicating essentially the same code over and over again.
A cleaner way to do this is to implement a while loop and standardize the code. The loop will call each item in sequence and check if it should continue processing for each step. As you can see this is a much cleaner way to implement a multi-step piece of code.
Subscribe to:
Posts (Atom)